Dedicated Servers
High Performance Hardware, Generous Bandwidth & Total Control. Safe, Reliable & Fast Dedicated Server Hosting
Dedicated servers — all to yourself and under your command.
Linux Dedicated Server Plans
Windows Dedicated Server Plans
Each Dedicated Server Plan includes:
- Free Rapid setup
- Bandwidth Overage Protection
- 3 Dedicated IPs
- Best-of-breed routers and servers
- TippingPoint® Intrusion Prevention Systems
- Telephone, email and Web-based tech support
- 24/7 physical security & network monitoring
- FTP & Root Access
- Choice of Operating Systems
- Install any script.
- Create cPanel/Plesk Accounts for clients
Our dedicated server plans feature lightning-fast processors, up to 32 GB of RAM, 20 TB of bandwidth, and Intel Core i3/i5/i7 processors, all backed by the best service and support in the industry, available LIVE 24/7. With our team of experts, you don’t have to worry about setup — we’ll get your server up and running fast! Choose the plan that’s right for you, then customize it to meet your unique needs with even more bandwidth, control panel options, backup plans, firewall protection and more.
Included Support
If the source of the technical problem you are experiencing lies within systems or technology under our exclusive management, no charge will apply.
Examples of supported technical problems:
- Your server becomes unreachable due to a network failure within our facility.
- Your server becomes unreachable due to a hardware failure within our facility.
- The hosting service setup process failed to complete successfully.
- A root user password change request failed to resolve successfully.
If you need custom work, such as Advanced scripting, programming or troubleshooting, you need our Assisted Service Plan or Expert Hands.
External Firewall Protection
Our Strong firewall solution controls the incoming and outgoing network traffic based on applied rule sets. It establishes a strong barrier between a trusted, secure internal network and external networks (e.g., the Internet) that is not assumed to be secure and trusted. It protects our servers from web based threats.
Cisco ASA 5505 Firewall: Keep hackers, worms and other cyber-threats from gaining access to your server. Our External Hardware Firewalls establish end-to-end encrypted VPN tunnels to securely connect server users and provide a greater level of security and increased performance than using only a software firewall (software firewalls are included in many control panels — such as our Parallels Plesk Panel).
The Cisco ® ASA 5500 Series Business Edition is an enterprise-strength comprehensive security solution that combines market-leading firewall, VPN, and optional content security capabilities, so you can feel confident your business is protected. This easy-to-use solution lets you control access to network resources to protect business data and maximize network uptime. Employee productivity is increased by controlling file sharing, instant messaging, spam, phishing, and other emerging threats. IT resources are freed from virus eradication and system cleanup activities. New business applications can be safely deployed without opening up security holes. Mobile employees and business partners can securely connect to your network over the Internet using IP Security (IPsec) or Secure Sockets Layer (SSL) VPN services. With a Cisco ASA 5500 Series solution protecting your network, you can focus on growing your business, without worrying about the latest security threats.

Cisco ASA 5505 Firewall Appliance The Internet has become a critical business tool for organizations of all sizes. It enables new opportunities for growth of the business. It provides connectivity with partners and remote workers via VPN connections. But it is also a conduit for threats to enter a company’s network. And these threats can have a significant impact on the business:
- Unauthorized access: Leads to loss of company data, unplanned downtime related liabilities.
- Reduce cleanup costs: Reduce the costly process of cleaning up spyware, viruses, and other malware.
- Viruses: Can infect systems, bringing them down and resulting in outages and lost revenue
- Spam and phishing: Creates a nuisance and contributes to loss of employee productivity
- Infected VPN traffic: Creates a vector for threats to enter the network and disrupt the business
RAID 1 Mirroring
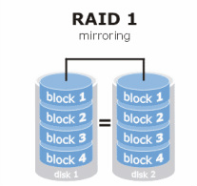
We use RAID 1 Mirroring technique, that creates an exact copy (or mirror) of a set of data on two disks. This is useful when read performance or reliability is more important than data storage capacity. Such an array can only be as big as the smallest member disk. These mirrors are usually used to guard against data loss due to drive failure. Each drive in a mirror contains an identical copy of the data. When an individual drive fails, the mirror continues to work, providing data from the drives that are still functioning.
RAID (Redundant Array of Independent Disks) levels are a basic set of RAID configurations that employ the techniques of striping, mirroring, or parity to create large reliable data stores from general purpose computer hard disk drives examples are RAID 0 (striping), RAID 1 (mirroring), RAID 5 (distributed parity) and RAID 6 (dual parity).
Advantages
- RAID 1 offers excellent read speed and a write-speed that is comparable to that of a single disk.
- In case a disk fails, data do not have to be rebuild, they just have to be copied to the replacement disk.
- RAID 1 is a very simple technology.
Dedicated IP Address

We provide Free Dedicated IP address with each Dedicated Server Plan. A dedicated IP address can help you to :
- Access your entire website via its IP address on any browser.
- Access your accounts by FTP or the Web when the domain name is otherwise inaccessible, such as during domain name propagation periods.
- Ensure faster response during periods of high traffic load, giving you less downtime.
- Set up your own private SSL protection on your website.
- Boost your search engine rankings.
- Avoid Spamming issues from other hosts on a shared IP address.